Describe What Encryption Is and Why It Is Used
End-to-end encryption E2EE is a system of communication where only the communicating users can read the messages. The rounds constants in AES are the value of 2 round_number modulo Galois Field 2 8.

Pin On Softmaker Office 2021 For Windows Macos And Linux
Finally the leftmost byte is exclusive-ored with a round constant.

. The San Bernardino Case. If the network interface card does not support MACsec the encryption is done on the main processor on the local computer. But put plainly password encryption works by putting your original word through a series of scrambling steps.
This article recognizes that some research projects and some areas of research are more likely to put. Follow edited Mar 20 2018 at 1921. To help test this hypothesis it would be useful if you could.
Scams and fraud are widespread on P2P payments app Zelle but the US banks backing the app say returning money to defrauded customers is not their responsibility Zelle the payments platform used by millions of customers is a popular target of scammers. Four main types of encryption exist. HTTP is used for transferring data between the client browser request and the web server response in the hypertext format same in case of HTTPS except that the transferring of data is done in an encrypted format.
Your system has a. In other words the encryption associated with the computer systems solutions and services used by federal government agencies must meet the minimum standards specified in FIPS PUB 140-2. Alex Beals Alex Beals.
Researchers shall describe measures for meeting confidentiality obligations and explain any reasonably foreseeable disclosure requirements. In application materials they submit to the REB. FYI it might not be a mathematical mapping but rather an index into a list of common names.
For many years we have used encryption to protect our customers personal data because we believe its the only way to keep their information safe. This has a huge impact on the IT procurement process as the only solution vendors that can be considered without obtaining a variance are those that have had their products. 219 1 1 gold badge 2 2 silver badges 5 5 bronze badges.
The terminology can be intimidating especially for people with no background in computer science. Asked Oct 13 2014 at 2126. A MACsec-capable switch is required on the network side.
It offers an excellent free plan and has more options than you can shake a stick at but suffers a little when it comes to usability. All of the components in the AnyConnect Secure Mobility Client can be used independently. The S-Box operation used in the AES key schedule is identical to the one used in the encryption phase as described previously.
During the consent process with prospective participants. Clickup is an interesting project management tool. So it can be said that https thwart hackers from interpretation or modification of data throughout the transfer of packets.
The CIA used a secret base in Munich initially on a military installation used by American troops and later in the attic of a building adjacent to the US. If you want to control encryption yourself you can use customer-managed encryption keys CMEK for BigQuery. CAN I USE THE ANYCONNECT NETWORK ACCESS MANAGER WITHOUT THE VPN FUNCTION.
Key encryption keys do not directly encrypt your data but are used to encrypt the data encryption keys that Google uses to encrypt your data. For more information see Cloud Key Management Service KMS. Consulate as the headquarters for its.
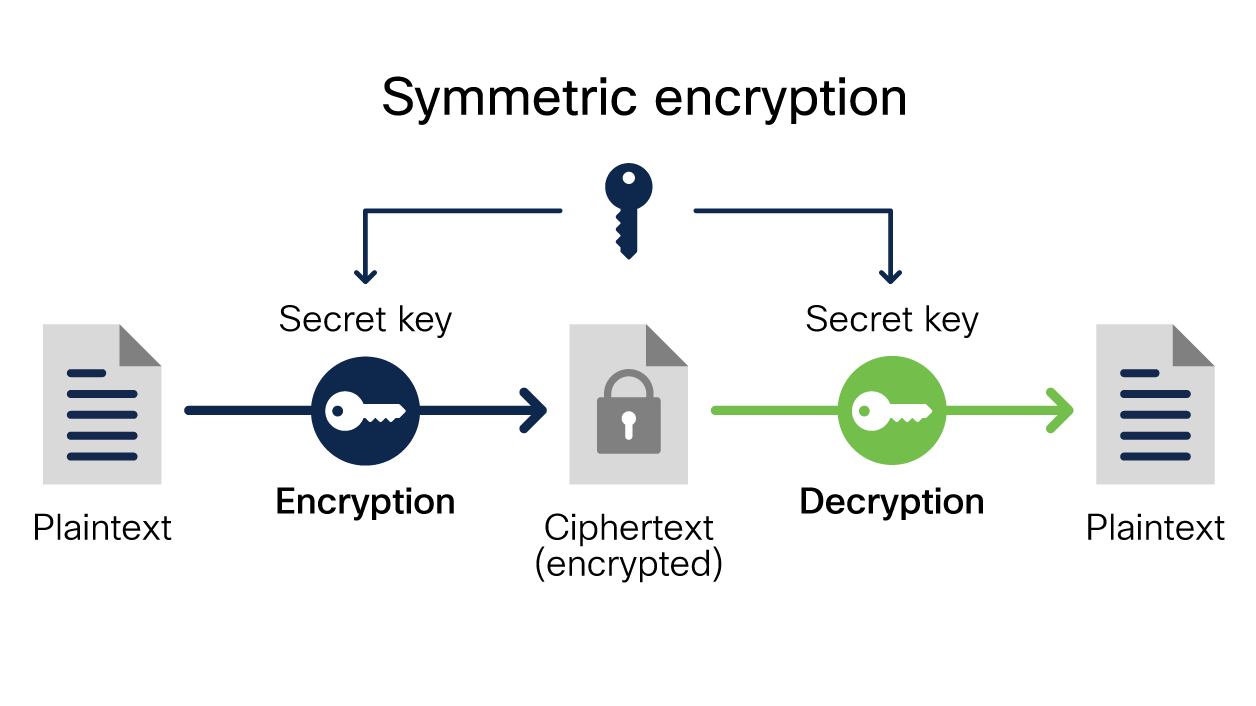
Experts use terms like salt SHA-1 and private key to describe what encryption is and how it works. That is why encryption has become so important to all of us. In the permutation phase of the g function each byte of the word is shifted one position to the left.
We have even put that data out of our own reach because we believe the contents of your iPhone are none of our business. In principle it prevents potential eavesdroppers including telecom providers Internet providers malicious state bodies and even the provider of the communication service from being able to access the cryptographic keys needed to decrypt. Telnet is a set of rules.

What Is Encryption Types Algorithms More Proofpoint Uk

Comments
Post a Comment